Manage and Protect Your Data
Automated security and governance controls for all data types in your on-prem, cloud, and hybrid environments.
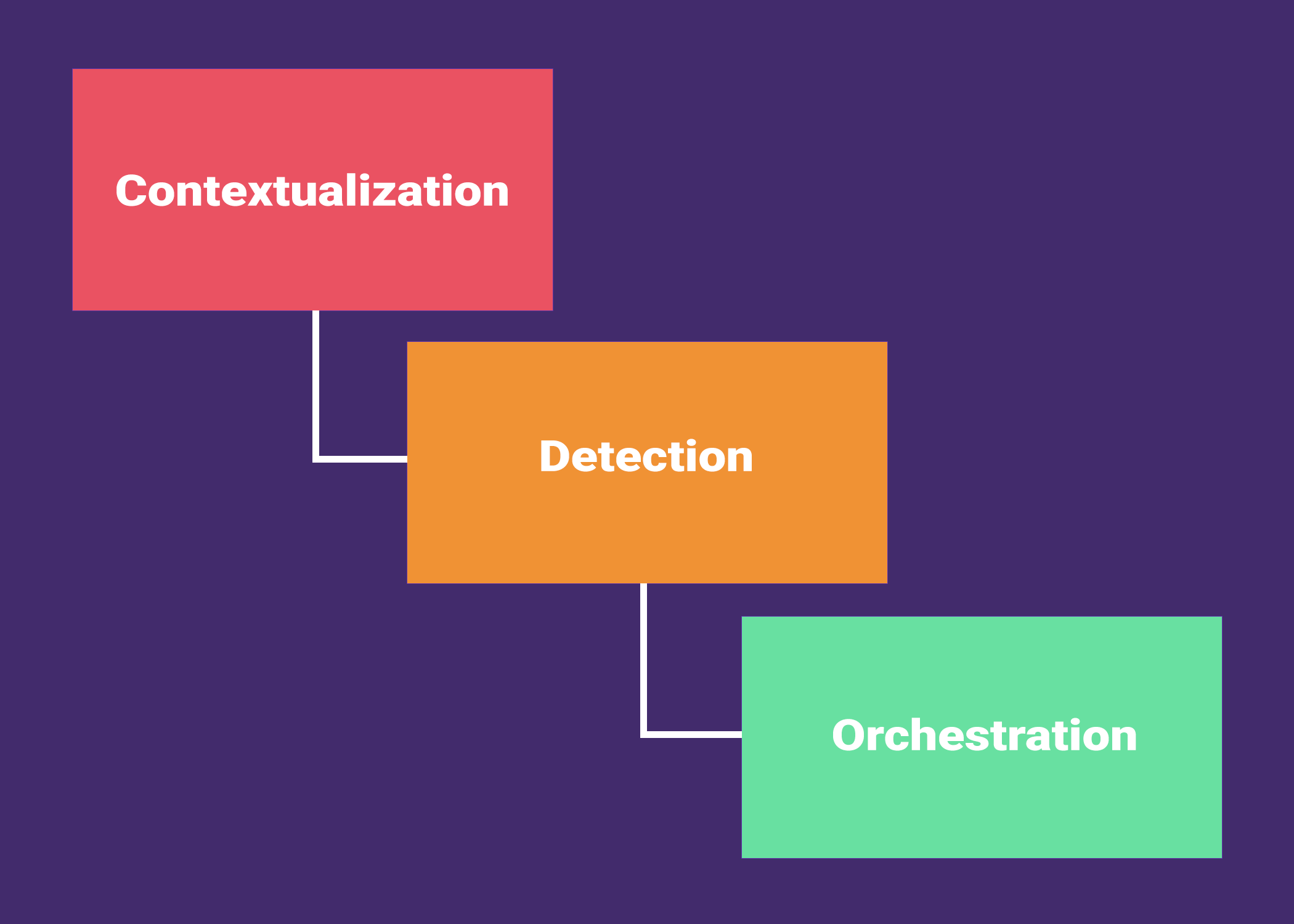
Security for your full data lifecycle
Enhancing Security Through Every Phase of Your Data Journey
-
Cloud Native, On-Prem, & Hybrid Ready
Cloud Native, On-Prem, & Hybrid Ready
Built for any environment. Secure your data across cloud, on-prem, and hybrid deployments
-
Automated Discovery and Protection
Automated Discovery and Protection
Automatically discover and secure your structured and unstructured data wherever it resides, zeroing in on the “unknowns” shadow data
-
Precise Data Classification and Sensitivity Tagging
Precise Data Classification and Sensitivity Tagging
Automated classification and tagging, Collect, analyze, and tag data to bolster security and compliance
-
Advanced Data Access and Usage Governance
Advanced Data Access and Usage Governance
Empower your organization with actionable insights into data access and usage, driving compliance and securing innovation.
-
Seamless Integrations
Seamless Integrations
Connect with ease. Integrate seamlessly with your existing security ecosystem.
Discover your data. Understand your business.
Gain actionable insights into your data’s infrastructure, types and attributes, users, and usage
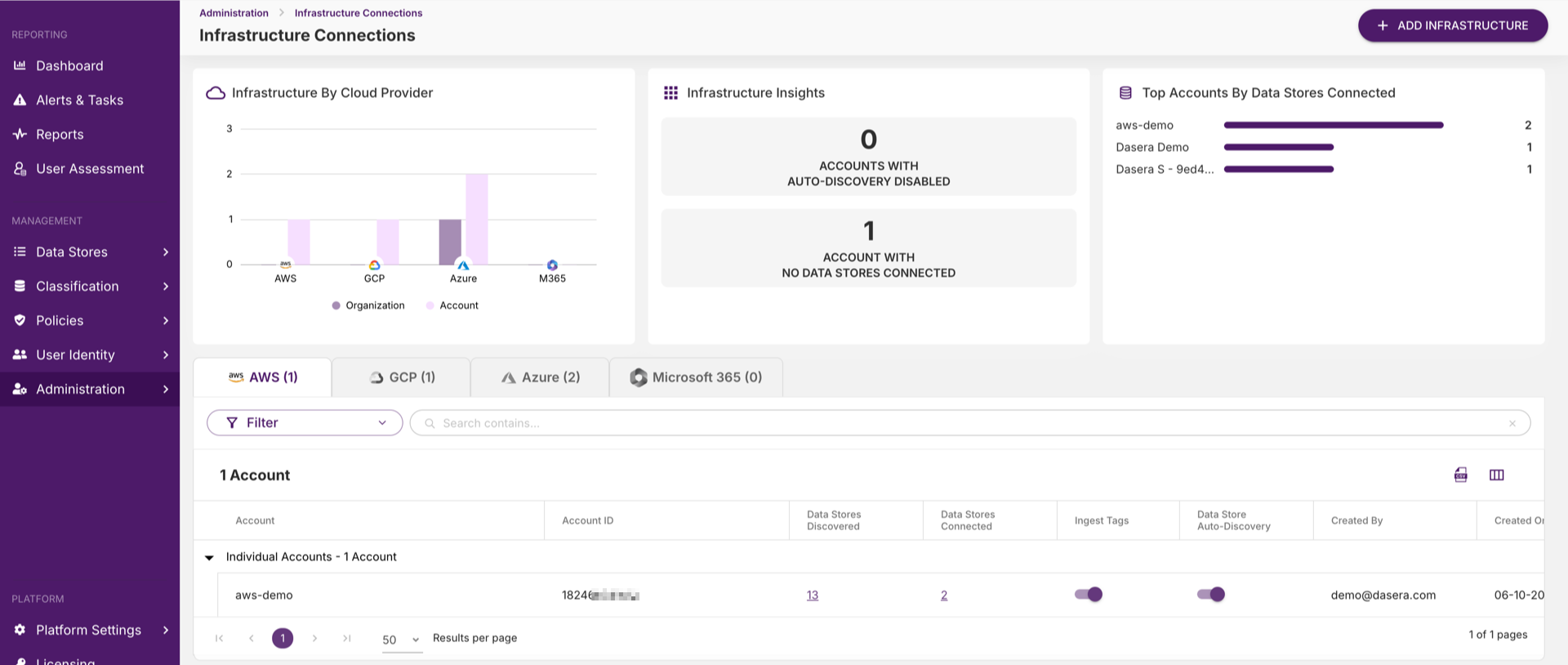
Data Infrastructure
Uncover the full extent of your data environment
- Discover shadow data stores across all environments
- Identify all sensitive data storage locations.
- Ensure proper cloud storage configurations.
- Apply end-to-end encryption for data at rest and in transit.
Data and Attributes
Pinpoint and prioritize your most sensitive data
- Identify all types of sensitive data
- Ensure accurate classification of data, from PII to proprietary
- Comply with data regulations such as GDPR, PCI-DSS, and HIPAA
- Adhere to data sovereignty laws in all operational regions
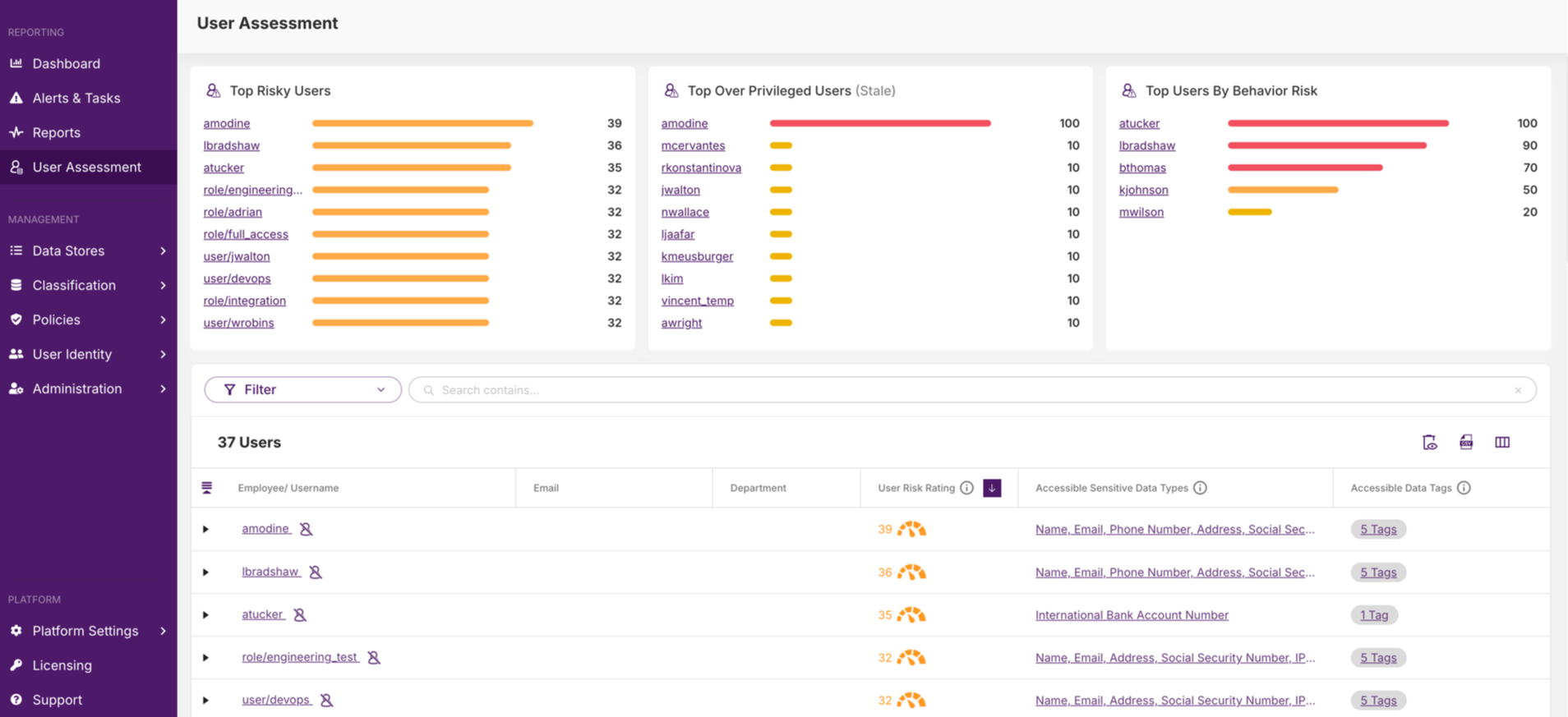
Data Users
Control who sees what, secure access & permissions
- Track sensitive data access by users and applications
- Establish robust controls for admin privileges
- Tailor user permissions to balance security with efficiency
- Quickly identify and respond to unauthorized data access
Data Usage
Monitor and secure every data interaction
- Set alerts for abnormal data transactions or query volumes.
- Enforce adherence to governance and regulatory standards in data usage.
- Differentiate between normal operations and potential security threats.
- Fortify the processing of sensitive data across all environments.
Frictionless Integration
Deploy in minutes and connect seamlessly to any data store across IaaS, PaaS, SaaS, and public, multi-cloud, on-premises, or hybrid environments.
- All
- AWS
- GCP
- AZURE
- MICROSOFT 365
- GOOGLE WORKSPACE
- CLOUD DATA PLATFORMS
- ADDITIONAL PLATFORMS
- BI TOOLS
- CNAPP
- ENTERPRISE RECOVERY AND BACKUP
- SIEM SOLUTIONS
- NOTIFICATIONS
- SSO PROVIDERS

Amazon Redshift
Visibility, governance, and protection for Amazon Redshift clusters

Amazon Aurora MySQL
Amazon Aurora is a global-scale relational database service built for the cloud with full MySQL compatibility.

Amazon Aurora PostgreSQL
Amazon Aurora is a global-scale relational database service built for the cloud with full Postgre SQL compatibility.

Amazon RDS Postgre SQL
With Amazon RDS, you can deploy scalable PostgreSQL deployments in minutes with cost-efficient and resizable hardware capacity.

Amazon RDS MySQL
With Amazon RDS, you can deploy scalable MySQL servers in minutes with cost-efficient and resizable hardware capacity.

Amazon RDS Maria DB
With Amazon RDS, you can deploy scalable MariaDB cloud databases in minutes with cost-efficient and resizable hardware capacity.

Amazon RDS Oracle
Amazon RDS for Oracle is a fully managed commercial database that makes it easy to set up, operate, and scale Oracle deployments in the cloud.

Amazon RDS Microsoft SQL Server
With Amazon RDS, you can deploy multiple editions of SQL Server (2014, 2016, 2017, 2019, and 2022), including Express, Web, Standard, and Enterprise, in minutes with cost-efficient and re-sizable compute capacity.

Amazon Athena
Amazon Athena is a serverless, interactive analytics service that provides a simplified and flexible way to analyze petabytes of data where it lives.

Amazon S3
Visibility, protection, and governance for Amazon S3 Buckets.

Amazon Dynamo DB
Amazon DynamoDB is a serverless, NoSQL database service that enables you to develop modern applications at any scale.

Amazon EBS
Amazon Elastic Block Store (EBS) is an easy to use, high-performance cloud Storage Area Network (SAN).

Amazon EFS
Amazon Elastic File System (EFS) provides a simple, scalable fully managed elastic NFS file system for AWS compute instances.

Big Query
Visibility, governance, and protection for Big Query

Cloud SQL MySQL
Visibility, governance, protection for Cloud SQL MySQL

Cloud SQL Postgre SQL
Visibility, governance, and protection for Cloud SQL Postgre SQL

Cloud SQL SQL Server
Visibility, governance, and protection for Cloud SQL SQL Server

Cloud Spanner
Visibility, governance, and protection for Cloud Spanner

Cloud Storage
Visibility, governance, and protection for Cloud Storage

Azure MySQL
Visibility, governance, and protection for Azure MySQL

Azure SQL Server
Visibility, protection, and governance for Azure SQL Server

Azure PostgreSQL
Visibility, governance, and protection for Azure PostgreSQL

Azure MariaDB
Visibility, governance, and protection for Azure MariaDB

Azure SQL Database
Visibility, governance, and protection for Azure SQL Database

Azure Synapse Analytics
Visibility, governance, and protection for Azure Synapse Analytics

Azure Databricks
Visibility, governance, and protections for Azure Databricks

Azure Blob Storage
Visibility, governance, and protection for Azure Blob Storage

Azure Files
Visibility, governance, and protection for Azure Files

OneDrive
Visibility, governance, and protection for OneDrive instances

SharePoint
Visibility, governance, and protection for SharePoint instances

Google Drive
Visibility, governance, and protection for Google Drive instances

Snowflake
Visibility, governance, and protection for Snowflake instances

Databricks
Visibility, governance, and protection for Databricks instances

Heroku Postgres
Visibility, governance, and protection for Heroku Postgres instances

mongoDB
Visibility, governance, and protection for mongoDB instances

SAP HANA
Visibility, governance, and protection for SAP HANA instances

Microsoft SQL Server
Visibility, governance, and protection for Microsoft SQL Server instances

PostgreSQL
Visibility, governance, and protection for PostgreSQL instances

Oracle
Visibility, governance, and protection for Oracle instances

MySQL
Visibility, governance, and protection for MySQL instances
Tableau
Visibility and governance for all Tableau users
Looker
Visibility and governance for all Looker users
Sisense
Visibility and governance for all Sisense users
Mode
Visibility and governance for all Mode Analytics users
Chartio
Visibility and governance for all Chartio users

Panoptica
Cisco’s cloud application security solution for code to cloud provides seamless scalability across clusters and multi-cloud environments.

Cohesity
Cohesity makes it easy to secure, protect, manage, and get value from data — across the data center, edge, and cloud.

Commvault
Commvault Cloud delivers true cloud cyber resilience while ensuring the fastest recovery. It is your best defense against ransomware at the best TCO.
Splunk
Send all Dasera security alerts to Splunk
SumoLogic
Send all Dasera security alerts to Sumo Logic
Datadog
Send all Dasera security alerts to Datadog
Logrhythm
Send all Dasera security alerts to Logrhythm

Amazon SNS
Send and syndicate all Dasera security alerts to Amazon Simple Notification Service (SNS)
Slack
Send Dasera security alerts to your team’s Slack channels
Google Pub/Sub
Send and syndicate all Dasera security alerts to Google Cloud Pub/Sub
Gmail
Send Dasera security alerts to your email
PagerDuty
Send Dasera security alerts to PagerDuty

Amazon SQS
Send Dasera security alerts to Amazon Simple Queue Service (SQS)
Azure Event Grid
Send and syndicate Dasera security alerts to Azure Event Grid
Okta
Leverage Okta for single sign-on into Dasera and employee directory information
Gsuite
Leverage G Suite for single sign-on into Dasera
Ping Identity
Leverage Ping Identity for single sign-on into Dasera
Microsoft Active Directory
Leverage Microsoft Active Directory for employee directory information
Onelogin
Leverage Onelogin for single sign-on into Dasera

Amazon Redshift
Visibility, governance, and protection for Amazon Redshift clusters

Amazon Aurora MySQL
Amazon Aurora is a global-scale relational database service built for the cloud with full MySQL compatibility.

Amazon Aurora PostgreSQL
Amazon Aurora is a global-scale relational database service built for the cloud with full Postgre SQL compatibility.

Amazon RDS Postgre SQL
With Amazon RDS, you can deploy scalable PostgreSQL deployments in minutes with cost-efficient and resizable hardware capacity.

Amazon RDS MySQL
With Amazon RDS, you can deploy scalable MySQL servers in minutes with cost-efficient and resizable hardware capacity.

Amazon RDS Maria DB
With Amazon RDS, you can deploy scalable MariaDB cloud databases in minutes with cost-efficient and resizable hardware capacity.

Amazon RDS Oracle
Amazon RDS for Oracle is a fully managed commercial database that makes it easy to set up, operate, and scale Oracle deployments in the cloud.

Amazon RDS Microsoft SQL Server
With Amazon RDS, you can deploy multiple editions of SQL Server (2014, 2016, 2017, 2019, and 2022), including Express, Web, Standard, and Enterprise, in minutes with cost-efficient and re-sizable compute capacity.

Amazon Athena
Amazon Athena is a serverless, interactive analytics service that provides a simplified and flexible way to analyze petabytes of data where it lives.

Amazon S3
Visibility, protection, and governance for Amazon S3 Buckets.

Amazon Dynamo DB
Amazon DynamoDB is a serverless, NoSQL database service that enables you to develop modern applications at any scale.

Amazon EBS
Amazon Elastic Block Store (EBS) is an easy to use, high-performance cloud Storage Area Network (SAN).

Amazon EFS
Amazon Elastic File System (EFS) provides a simple, scalable fully managed elastic NFS file system for AWS compute instances.

Big Query
Visibility, governance, and protection for Big Query

Cloud SQL MySQL
Visibility, governance, protection for Cloud SQL MySQL

Cloud SQL Postgre SQL
Visibility, governance, and protection for Cloud SQL Postgre SQL

Cloud SQL SQL Server
Visibility, governance, and protection for Cloud SQL SQL Server

Cloud Spanner
Visibility, governance, and protection for Cloud Spanner

Cloud Storage
Visibility, governance, and protection for Cloud Storage

Azure MySQL
Visibility, governance, and protection for Azure MySQL

Azure SQL Server
Visibility, protection, and governance for Azure SQL Server

Azure PostgreSQL
Visibility, governance, and protection for Azure PostgreSQL

Azure MariaDB
Visibility, governance, and protection for Azure MariaDB

Azure SQL Database
Visibility, governance, and protection for Azure SQL Database

Azure Synapse Analytics
Visibility, governance, and protection for Azure Synapse Analytics

Azure Databricks
Visibility, governance, and protections for Azure Databricks

Azure Blob Storage
Visibility, governance, and protection for Azure Blob Storage

Azure Files
Visibility, governance, and protection for Azure Files

OneDrive
Visibility, governance, and protection for OneDrive instances

SharePoint
Visibility, governance, and protection for SharePoint instances

Google Drive
Visibility, governance, and protection for Google Drive instances

Snowflake
Visibility, governance, and protection for Snowflake instances

Databricks
Visibility, governance, and protection for Databricks instances

Heroku Postgres
Visibility, governance, and protection for Heroku Postgres instances

mongoDB
Visibility, governance, and protection for mongoDB instances

SAP HANA
Visibility, governance, and protection for SAP HANA instances

Microsoft SQL Server
Visibility, governance, and protection for Microsoft SQL Server instances

PostgreSQL
Visibility, governance, and protection for PostgreSQL instances

Oracle
Visibility, governance, and protection for Oracle instances

MySQL
Visibility, governance, and protection for MySQL instances
Tableau
Visibility and governance for all Tableau users
Looker
Visibility and governance for all Looker users
Sisense
Visibility and governance for all Sisense users
Mode
Visibility and governance for all Mode Analytics users
Chartio
Visibility and governance for all Chartio users

Panoptica
Cisco’s cloud application security solution for code to cloud provides seamless scalability across clusters and multi-cloud environments.

Cohesity
Cohesity makes it easy to secure, protect, manage, and get value from data — across the data center, edge, and cloud.

Commvault
Commvault Cloud delivers true cloud cyber resilience while ensuring the fastest recovery. It is your best defense against ransomware at the best TCO.
Splunk
Send all Dasera security alerts to Splunk
SumoLogic
Send all Dasera security alerts to Sumo Logic
Datadog
Send all Dasera security alerts to Datadog
Logrhythm
Send all Dasera security alerts to Logrhythm

Amazon SNS
Send and syndicate all Dasera security alerts to Amazon Simple Notification Service (SNS)
Slack
Send Dasera security alerts to your team’s Slack channels
Google Pub/Sub
Send and syndicate all Dasera security alerts to Google Cloud Pub/Sub
Gmail
Send Dasera security alerts to your email
PagerDuty
Send Dasera security alerts to PagerDuty

Amazon SQS
Send Dasera security alerts to Amazon Simple Queue Service (SQS)
Azure Event Grid
Send and syndicate Dasera security alerts to Azure Event Grid
Okta
Leverage Okta for single sign-on into Dasera and employee directory information
Gsuite
Leverage G Suite for single sign-on into Dasera
Ping Identity
Leverage Ping Identity for single sign-on into Dasera
Microsoft Active Directory
Leverage Microsoft Active Directory for employee directory information
Onelogin
Leverage Onelogin for single sign-on into Dasera
Explore Our Featured Resources!
Read the latest on how Dasera is changing the story.